What is Vault?
Vault is an identity-based secrets and encryption management system. Vault provides encryption services that are gated by authentication and authorization methods. Using Vault’s UI, CLI, or HTTP API, access to secrets and other sensitive data can be securely stored and managed, tightly controlled (restricted), and auditable
How to install Vault
install the precompiled binary, download the applicable package for your system. Vault is packaged as a zip file. Once the zip is downloaded, unzip the file into your designated directory. The vault binary inside is all that is necessary to run Vault (or vault.exe for Windows). No additional files are required to run Vault. Copy the binary to your system. If you intend to access it from the command-line, ensure that you place the binary somewhere on your PATH. Refer to the HashiCorp Tutorials to start a server, put your first secret, and use other features of Vault.
1 .How to install Vault

2. After downloading the file, Unzip the file/package.

3. Now you can install vault. Double click vault.exe
4. After installing vault, make sure to add it on your PATH. See this page on how to set PATH for linux and MAC and windows.
Verify vault installation
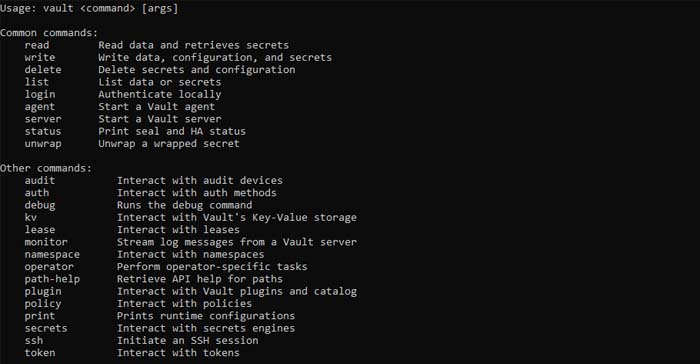
After installation, to verify vault if installed without problem, open new terminal then try the command vault. You should see help output similar to the following
$ vault
Output:
Start Vault Developer mode
You can start Vault as a server in “dev” mode like so: vault server -dev. This dev-mode server requires no further setup, and your local vault CLI will be authenticated to talk to it. This makes it easy to experiment with Vault or start a Vault instance for development. Every feature of Vault is available in “dev” mode. The -dev flag just short-circuits a lot of setup to insecure defaults.
$ vault server -dev
Output:
==> Vault server configuration:
Api Address: http://127.0.0.1:8200
Cgo: disabled
Cluster Address: http://127.0.0.1:8200
Go Version: go1.17.2
Listener 1 : tcp ( addr: "127.0.0.1:8200" ,
cluster address: "127.0.0.1:8201" ,
max_request_duration: "1m30s" ,
max_request_size: "33554432" ,
tls: "disabled" )
Log Level: info
Mlock: supported: false , enabled: false
Recovery Mode: false
Storage: inmem
Version: Vault v1.9.4
Version Sha: fcbe948b2542a13ee8036ad07dd8ebf8554f56cb
== > Vault server started! Log data will stream in below:
WARNING! dev mode is enabled! In this mode, Vault runs entirely in -memory
and starts unsealed with a single unseal key. The root token is already
authenticated to the CLI, so you can immediately begin using Vault.
You may need to set the following environment variable:
Powershell:
$ env:VAULT_ADDR= 'http://127.0.0.1:8200'
cmd.exe:
set VAULT_ADDR= 'http://127.0.0.1:8200'
The unseal key and root token are displayed below in case you want to
seal/unseal the Vault or re-authenticate.
Unseal Key: BpUg6LVzQP3b8nIhIIZWvQ0Q5FuU63Dq0PyKuQsD/Qw=
Root Token: s. PrJcwT6kkUfG3kJdfhenoN9a
Development mode should NOT be used in production installations!
The dev server is a built-in, pre-configured server that is not very secure but useful for playing with Vault locally.
Adding Server Details in your PATH:
Open new terminal and make sure to have a copy of your unseal key and root token because in -dev mode it will change everytime you restart the server
CMD:
$ set VAULT_ADDR= 'http://127.0.0.1:8200'
$ set VAULT_TOKEN= 's.PrJcwT6kkUfG3kJdfhenoN9a'
Powershell:
$env:VAULT_ADDR= "http://127.0.0.1:8200"
$env:VAULT_TOKEN= "s.PrJcwT6kkUfG3kJdfhenoN9a"
When running Vault in dev mode, Key/Value v2 secrets engine is enabled at secret/ path. Key/Value secrets engine is a generic key-value store used to store arbitrary secrets within the configured physical storage for Vault. Secrets written to Vault are encrypted and then written to backend storage. Therefore, the backend storage mechanism never sees the unencrypted value and doesn’t have the means necessary to decrypt it without Vault
Accessing Vault:
Vault provides multiple mechanisms like UI, Cli and API to store/get the secrets.
To access the UI, open https://127.0.0.1:8200 in your browser.
Login using the root token given
Creating a secret to kv using python
“Development mode server stores all secrets in-memory, the moment the server restart or end all the secrets are deleted.”
Install HVAC:
$ pip install hvac
Connect to server
import hvac
def init_server () :
client = hvac.Client ( url = 'http://localhost:8200' )
print ( client . sys . is_initialized () )
init_server ()
Output:
True
Create your first secret
import hvac
def init_server () :
client = hvac.Client ( url = 'http://localhost:8200' )
create_secret ( client )
def create_secret ( client ) :
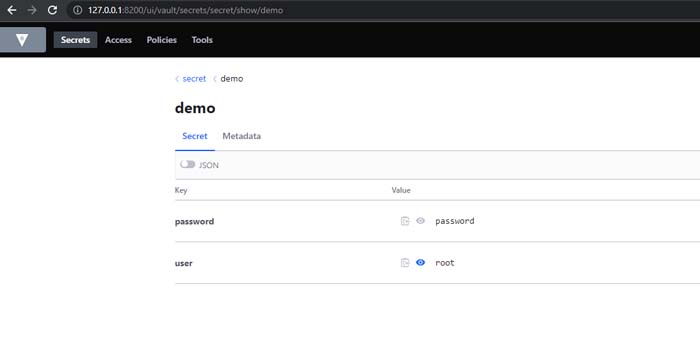
create_secret = client .secrets.kv.v2. create_or_update_secret ( path = 'demo' ,
secret = dict ( user = 'root' , password = 'password' ) )
print ( create_response )
init_server ()
Output:
{
'request_id': '81a1089b-2594-1089-57bb-a773509f1693' ,
'lease_id': '' ,
'renewable': False ,
'lease_duration': 0 ,
'data': {
'created_time': '2022-09-14T06:59:12.8146482Z' ,
'custom_metadata': None ,
'deletion_time': '' ,
'destroyed': False ,
'version': 2
} ,
'wrap_info': None ,
'warnings': None ,
'auth': None
}
Check Secret on UI
Check Secret using Cli
import hvac
def init_server () :
client = hvac.Client ( url = 'http://localhost:8200' )
show_secret ( client )
def show_secret ( client ) :
response = client .secrets.kv.v2. read_secret_version ( path = 'demo' )
print ( response [ ' data ' ] [ ' data ' ] )
init_server ()
Output:
{
'password':'pasword123' ,
'user':'root'
}
Vault other functionality
To learn more about it, explore the links in the references section.

